
Technical Advisory – Multiple Vulnerabilities in Faronics Insight (CVE-2023-28344, CVE-2023-28345, CVE-2023-28346, CVE-2023-28347, CVE-2023-28348, CVE-2023-28349, CVE-2023-28350, CVE-2023-28351, CVE-2023-28352, CVE-2023-28353) | NCC Group Research Blog ...

Metastealer – filling the Racoon void | NCC Group Research Blog | Making the world safer and more secure
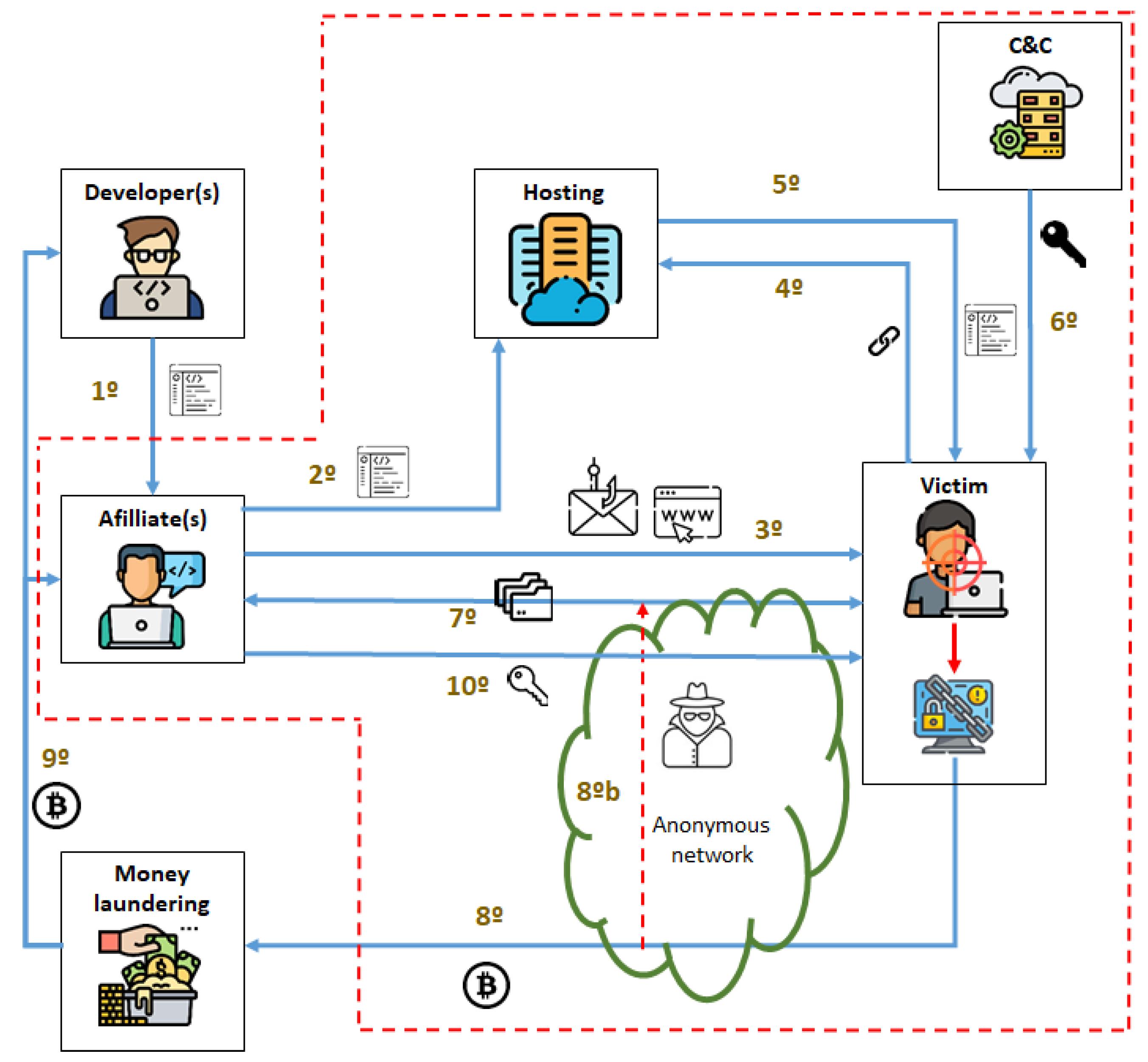
Electronics | Free Full-Text | Crypto-Ransomware: A Revision of the State of the Art, Advances and Challenges

Efficacy of Multiple Exercise Therapy after Coronary Artery Bypass Graft: A Systematic Review of Randomized Control Trials
![Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco](https://www.cisco.com/c/dam/en/us/td/i/300001-400000/350001-360000/356001-357000/356760.jpg)
Cisco Identity Services Engine Administrator Guide, Release 3.2 - Basic Setup [Cisco Identity Services Engine] - Cisco

Processes | Free Full-Text | A Survey on Programmable Logic Controller Vulnerabilities, Attacks, Detections, and Forensics
Submission of the WannaCry executable to VirusTotal with generated hashes. | Download Scientific Diagram
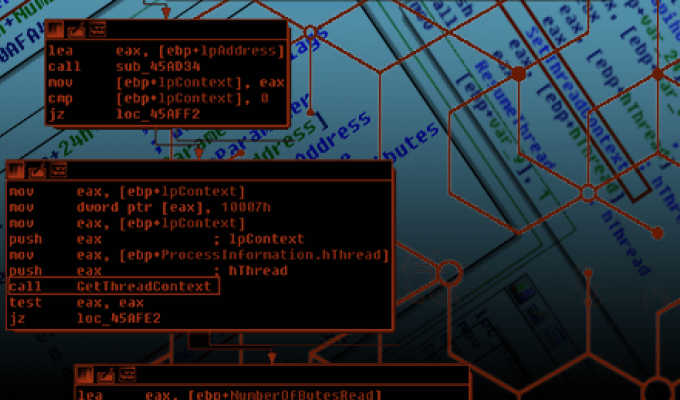
Ten process injection techniques: A technical survey of common and trending process injection techniques | Elastic Blog
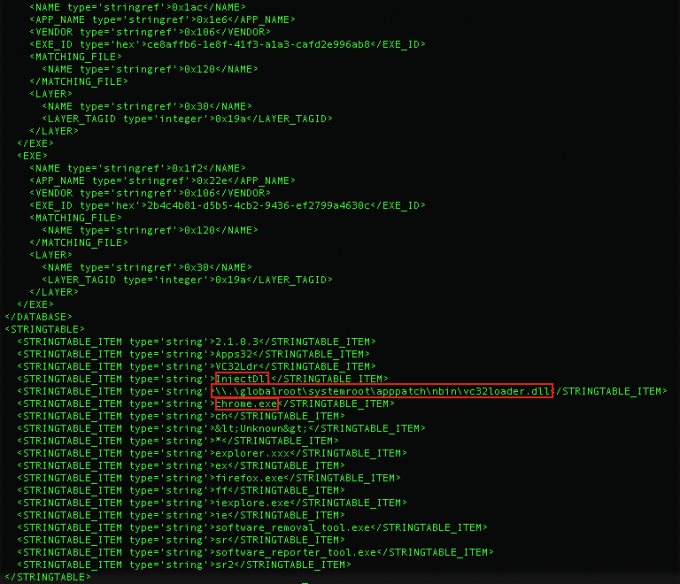
Ten process injection techniques: A technical survey of common and trending process injection techniques | Elastic Blog
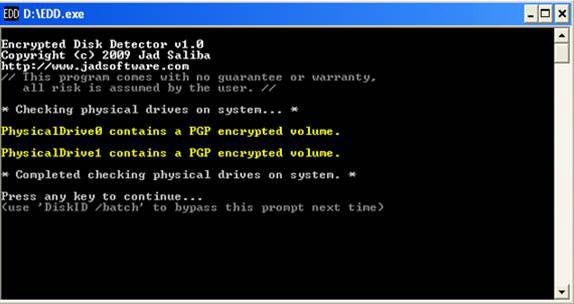
SANS Digital Forensics and Incident Response Blog | Help Improve EDD - Encrypted Disk Detector! | SANS Institute
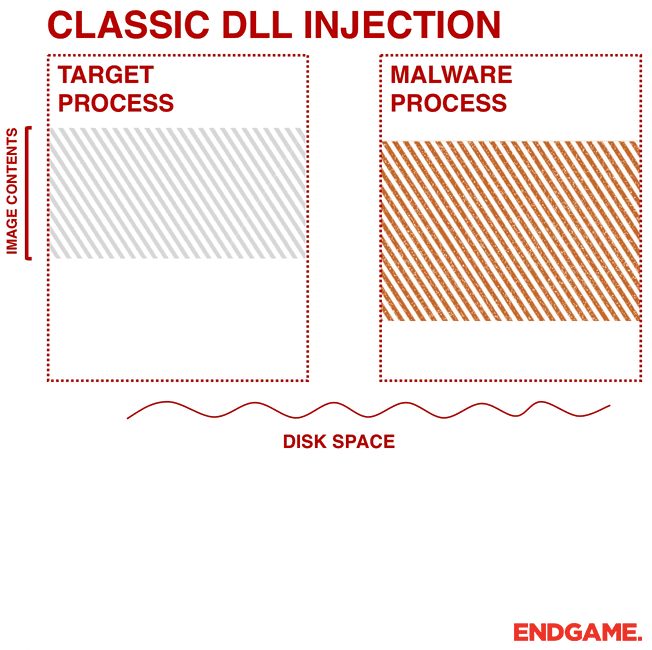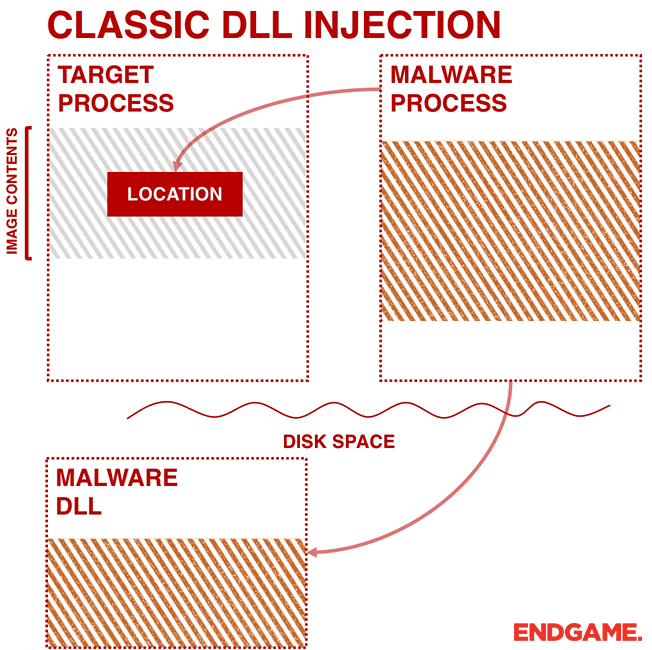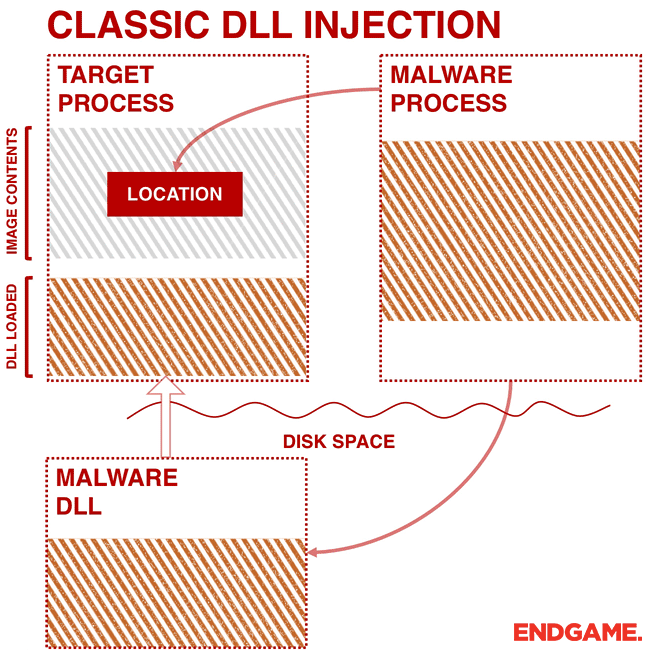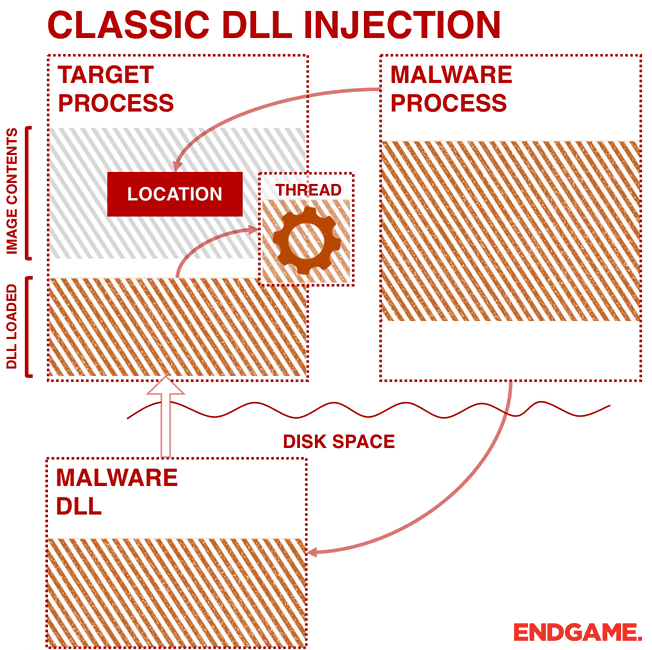
Ten process injection techniques: A technical survey of common and trending process injection techniques | Elastic Blog

Writing Exploits for Win32 Systems from Scratch | NCC Group Research Blog | Making the world safer and more secure





![PDF] A survey of Hardware-based Control Flow Integrity (CFI) | Semantic Scholar PDF] A survey of Hardware-based Control Flow Integrity (CFI) | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/1380ccde417df861d9c08d6d4194269fcff090bf/6-Figure1-1.png)

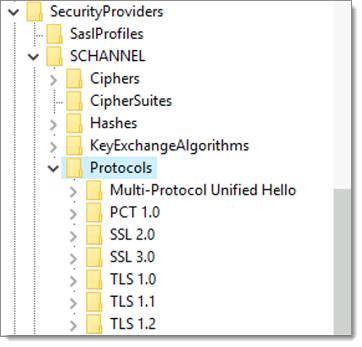
![On the classification of Microsoft-Windows ransomware using hardware profile [PeerJ] On the classification of Microsoft-Windows ransomware using hardware profile [PeerJ]](https://dfzljdn9uc3pi.cloudfront.net/2021/cs-361/1/fig-2-full.png)